JAKARTA, cssmayo.com – In an increasingly digital world, cybersecurity risk assessment has become a critical component of organizational security strategy. With cyber threats evolving rapidly, identifying vulnerabilities and understanding potential risks is essential for protecting sensitive information and maintaining business continuity. This guide provides a detailed approach to conducting effective cybersecurity risk assessments, empowering you to safeguard your organization like a pro.
Understanding Cybersecurity Risk Assessment
A cybersecurity risk assessment is a structured process designed to identify, evaluate, and prioritize risks to an organization’s information systems and data. This process involves assessing potential threats, vulnerabilities, and the impact of security breaches, allowing organizations to implement appropriate controls and mitigation strategies.
Key Steps in Conducting a Cybersecurity Risk Assessment

1. Define the Scope and Objectives
- Identify Assets: Determine which assets (hardware, software, data) are critical to the organization and require protection.
- Set Objectives: Clearly outline the goals of the risk assessment, such as compliance with regulations, improving security posture, or protecting customer data.
2. Identify Potential Threats
- Threat Modeling: Use threat modeling techniques to identify potential threats that could exploit vulnerabilities in your systems. Common threats include:
- Malware: Viruses, worms, and ransomware that can compromise systems.
- Phishing Attacks: Social engineering tactics aimed at tricking users into revealing sensitive information.
- Insider Threats: Employees or contractors who may intentionally or unintentionally cause harm to the organization.
3. Assess Vulnerabilities
- Vulnerability Scanning: Utilize automated tools to scan systems and networks for known vulnerabilities. This includes outdated software, misconfigurations, and weak passwords.
- Manual Assessment: Conduct manual reviews of security policies, access controls, and system configurations to identify potential weaknesses that automated tools may overlook.
4. Evaluate Risks
- Risk Analysis: Assess the likelihood of identified threats exploiting vulnerabilities and the potential impact on the organization. This can be done using qualitative or quantitative methods:
- Qualitative Analysis: Categorize risks as low, medium, or high based on expert judgment and experience.
- Quantitative Analysis: Assign numerical values to risks based on potential financial losses, allowing for a more objective evaluation.
5. Prioritize Risks
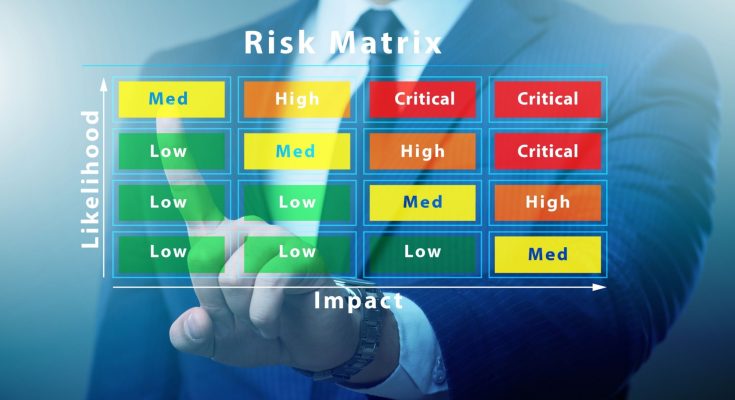
- Risk Matrix: Create a risk matrix to visualize and prioritize risks based on their likelihood and impact. This helps in determining which risks require immediate attention and resources.
- Focus on Critical Risks: Concentrate on the most significant risks that could have the greatest impact on the organization’s operations and reputation.
6. Develop Mitigation Strategies
- Implement Controls: Develop and implement security controls to mitigate identified risks. Common controls include:
- Firewalls and Intrusion Detection Systems: Protect networks from unauthorized access and monitor for suspicious activity.
- Access Controls: Limit access to sensitive information based on the principle of least privilege.
- Security Awareness Training: Educate employees on recognizing and responding to cybersecurity threats.
- Incident Response Plan: Establish an incident response plan to ensure a swift and effective response to security breaches.
7. Monitor and Review
- Continuous Monitoring: Regularly monitor systems and networks for new vulnerabilities and emerging threats. Use security information and event management (SIEM) tools for real-time monitoring.
- Periodic Assessments: Conduct regular risk assessments to adapt to changing threat landscapes and ensure that security measures remain effective.
Best Practices for Effective Cybersecurity Risk Assessment
1. Involve Stakeholders
Engage key stakeholders from various departments (IT, legal, compliance, operations) to ensure a comprehensive understanding of risks and to foster a culture of security awareness.
2. Stay Informed
Keep up-to-date with the latest cybersecurity trends, threats, and best practices. Subscribe to industry publications, attend conferences, and participate in training programs.
3. Document Everything
Thoroughly document the risk assessment process, findings, and mitigation strategies. This not only helps in tracking progress but also serves as a reference for future assessments.
4. Use a Framework
Consider using established frameworks such as NIST Cybersecurity Framework, ISO 27001, or CIS Controls to guide your risk assessment process and ensure a structured approach.
Conclusion
Conducting a thorough cybersecurity risk assessment is essential for identifying vulnerabilities and protecting your organization from cyber threats. By following a systematic approach, involving stakeholders, and implementing effective mitigation strategies, you can enhance your organization’s security posture and resilience against cyber attacks.
As cyber threats continue to evolve, regular risk assessments will be crucial in adapting to new challenges and safeguarding sensitive information. With this guide, you are equipped to identify vulnerabilities like a pro and strengthen your organization’s defenses.
Elevate Your Competence: Uncover Our Insights on Techno
Read Our Most Recent Article About Smart City Technologies!